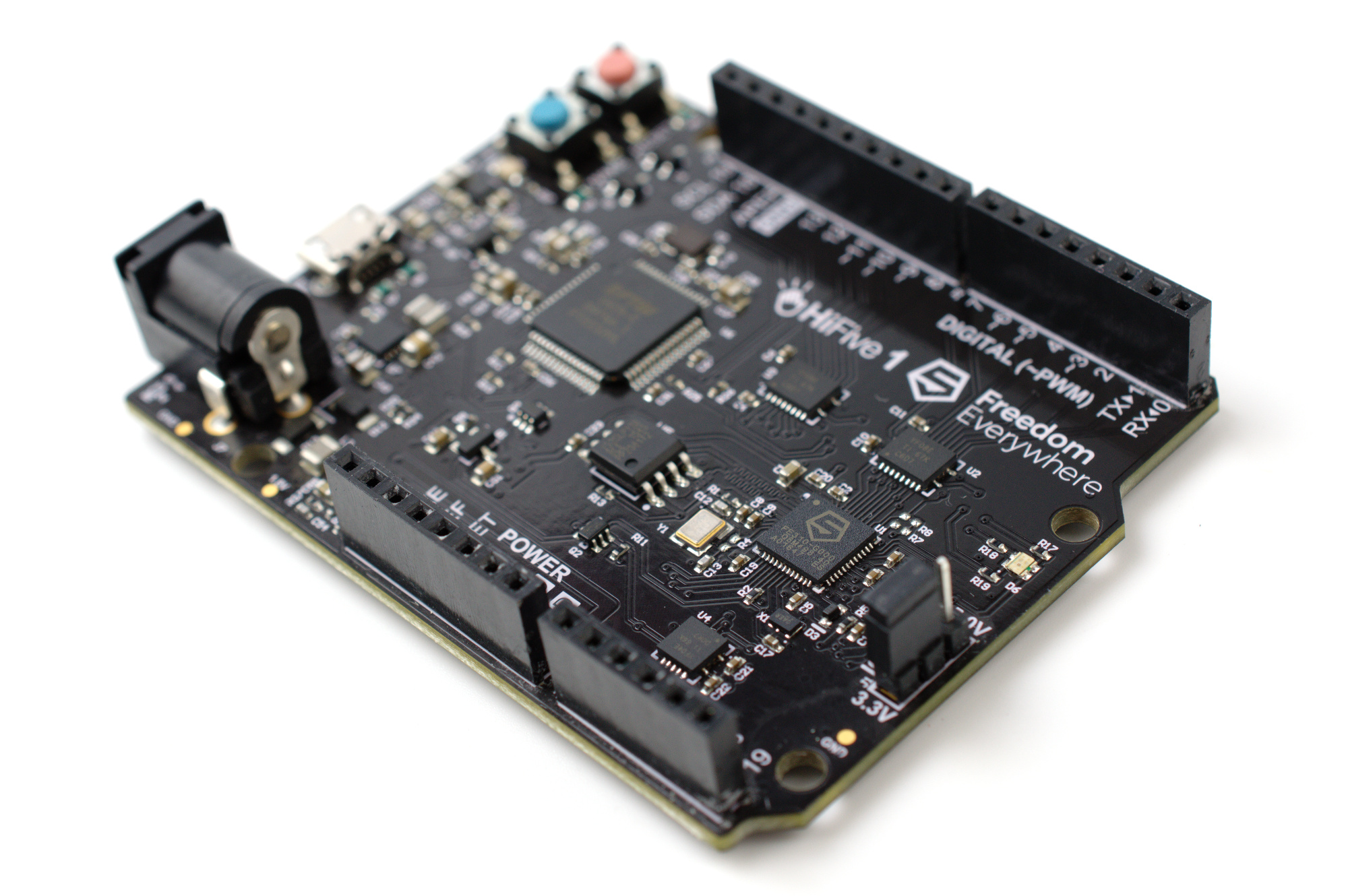
The GNU Compiler Collection (GCC) has hit version 7.1 and now includes support for the RISC-V instruction set architecture (ISA), three decades after the toolkit’s initial 1.0 release.
That support for the burgeoning RISC-V open instruction set architecture was coming to GCC was no secret, following the acceptance by the GCC Steering Committee of a port back in January this year. The need for some last-minute polish to the documentation and full adoption of the GCC coding standards delayed its public release, however, and while GCC 7.0 came and went without official support GCC 7.1 has it natively for the first time.
Maintained by Palmer Dabbelt and Andrew Waterman, the GCC RISC-V port offers native support for compiling code into 32-bit and 64-bit RISC-V binaries. GCC 7.1 also includes a range of other changes and improvements, including additional optimisations for size and performance, a fix for a longstanding though unusual bug when compiling AAPCS procedure calls for an ARM target, and improved support for OpenACC in C, C++, and Fortran.
Those developing with a RISC-V target in mind, meanwhile, can now benefit from Dave Patterson and John Hennessy’s joint experience thanks to the impending publication of Computer Organisation and Design RISC-V edition.
Updated specifically for the RISC-V architecture, this new edition of a well-regarded entry in the Morgan Kaufmann Series in Computer Architecture and Design has been updated with modern embedded computing – or, as its authors would have it, the “post-PC era” – at its forefront. Although billed as the “RISC-V Edition,” the book’s existing content has not been supplanted: the publication includes coverage of RISC-V alongside x86 and ARM, the latter two architectures focusing more on their core markets of mainstream and cloud computing and mobile devices respectively.
The new edition is available to buy now in the US from Amazon.com, while Amazon.co.uk has its UK release scheduled for the 26th of May. Those looking to order a copy from their local bookseller, meanwhile, can find it under ISBN-13 978-0128122754.
RISC-V pioneer SiFive, meanwhile, has announced a new business model for its Coreplex RISC-V IP, offering free access to documentation but requiring a one-time licensing fee for implementation.
“As an engineer, trying to get information from your average IP vendor is an exercise in futility,” claimed Yunsup Lee, chief technical officer and co-founder at SiFive, during the announcement. “The countless number of NDAs, partial answers and sales meetings you must agree to just to get basic evaluation material makes it feel like they don’t want your business. It’s unbelievable how far behind the industry is compared to the ease in which SaaS companies provide their products. When we founded SiFive, we wanted to change that. Through our ‘study-evaluate-buy’ model, we’ve made Coreplex IP licensing as easy as buying a subscription to any modern software service.”
Under the company’s new licence-based model, documentation and datasheets for its E31 Coreplex and E51 Coreplex – 32-bit and 64-bit respectively – RISC-V cores are made freely available for study, while access to RTL or an FPGA bitstream is provided upon registration. Should a developer wish to go ahead with implementation, the company charges a one-time $300,000 fee for the E31 and $600,000 for the E51 (£232,000 and £464,000 respectively.) This fee, SiFive has pointed out, is payable through the company’s website in what it claims is the first example of the ability to licence a processor core IP as quickly and easily – if not as affordably – as buying a book or takeaway.
The FOSSi Foundation has announced six participants in Google’s Summer of Code (GSOC) programme, including one who will be working with AB Open’s Andrew Back on a RISC-V core for the LimeSDR software defined radio.
Cairo Caplan, the Foundation has confirmed, has been officially accepted to the Google Summer of Code and will be working on development of a RISC-V CPU core which can be implemented on the field-programmable gate array (FPGA) present on the open-source LimeSDR software defined radio board. In this endeavour, Cairo is to be mentored by AB Open’s Andrew Back alongside Olof Kindgren and Zack Tamosevicius. The final goal: to replace the proprietary NIOS II softcore CPU with an open RISC-V core and have a fully open FPGA platform for the first time.
In a final bit of RISC-V news, the agenda for the sixth annual RISC-V Workshop has been finalised and posted to the website this week.
Set to take place between the 8th and 11th of May in Shanghai, the agenda for the RISC-V Workshop is absolutely packed. The four-day event begins with an all-day introduction to RISC-V, including a history from Dave Patterson, an explanatory presentation from Krste Asanovic, an introduction to the RISC-V Foundation from executive director Rick O’Connor, followed by presentations and a mini trade show from Foundation member companies.
The second and third days of the event offer more detailed presentations on specific RISC-V projects, ranging from a discussion on implementing RISC-V in application-specific integrated circuits (ASICs) and the look at the open-source SCR1 microcontroller from Syntacore to an update on the memory consistency model recently overhauled following the discovery of access ordering issues. Full details are available from the official website.
Linus Torvalds has officially released Linux 4.11 following a last-minute delay for a final release candidate, adding in a range of improvements and new features of interest to embedded developers.
As is usually the case, many of the new features of most interest to the embedded community come courtesy Free Electrons and are summarised on the official blog. These include power-saving improvements to suspend and resume and memory control on Atmel’s SAM processor family, higher data rates for the MMC controller on Allwinner platforms, power supply drivers for the AXP20X and AXP22X power management integrated circuits (PMICs), support for real-time clocks and Ethernet switches built into multiple Marvell Armada system-on-chips (SoCs), and support for the video encoder built into Broadcom’s BCM283x family.
As always, the latest mainline kernel – along with stable, longterm, and linux-next ‘bleeding edge’ releases – can be found on the Linux Kernel Archives page.
The Linux Foundation has announced the EdgeX Foundry, in what it describes as an attempt to unify the Internet of Things (IoT) marketplace and accelerate enterprise-grade IoT deployments.
“Success in Internet of Things is dependent on having a healthy ecosystem that can deliver interoperability and drive digital transformation,” claimed Jim Zemlin, the Linux Foundation’s executive director, at the announcement. “EdgeX Foundry is aligning market leaders around a common framework, which will drive IoT adoption and enable businesses to focus on developing innovative use cases that impact the bottom line.”
The EdgeX Foundry aims to build an ecosystem of companies rallying around a common open framework with a focus on edge computing, based on Dell’s FUSE source code licensed under the permissive Apache Licence 2.0. Founding members have been confirmed as including AMD, Analog Devices, Canonical, Linaro, and VMware. “Businesses currently have to invest a lot of time and energy into developing their own edge computing solutions, before they can even deploy IoT solutions to address business challenges,” claimed Philip DesAutels, senior director of IoT at the Linux Foundation. “EdgeX will foster an ecosystem of interoperable components from a variety of vendors, so that resources can be spent on driving business value instead of combining and integrating IoT components.”
Full details are available on the official website.
IoT developers are being warned of a new malware dubbed BrickerBot, which attacks vulenrable embedded devices to wipe its firmware in what security researchers are calling a “Permanent Denial of Service (PDoS) attack.”
First spotted and analysed by security firm Radware, BrickerBot attempts to log in to insecure IoT systems via the Telnet protocol before wiping all storage, bringing down its network connection, and powering off the system in such a way that it cannot be reactivated without a fresh firmware install. An initial attack, categorised as BrickerBot.1, was described by the company as “intense [and] short-lived,” while a second attack dubbed BrickerBot.2 and using The Onion Router (TOR) network is still ongoing.
Radware’s advice for protecting systems from BrickerBot and similar malware is simple: disabling Telnet access, changing from pre-configured factory-set and shared credentials, and using tools such as network and user/entity behavioural analysis (UEBA) to detect anomalous traffic and activity.
Finally, Felix Domke has requested assistance with an impressive project: an entirely open-source firmware replacement for Rigol DS10-family digital storage oscilloscopes (DSOs).
“The motivation for this effort is that the Rigol DS10xxZ is a dirt-cheap scope with okay-ish hardware that’s hackable,” Felix explained in his introductory post on the EEV Blog. “Other scopes either have inferior hardware, are more expensive, have weird application processor architectures for which no open toolchains (compiler, debugger, infrastructure in general) exist, or use ASICs. The DS10xxZ is in sweet spot where it’s affordable, uses off-the-shelf chips, ARM architecture, Xilinx Spartan-6 FPGA (for which a free toolchain exists), and is decently-spec’ed. I understand there are other scopes which are similar, but it seems the Rigol one is most popular.”
Thus far, Felix has Linux booting on the system – no mean feat – with access to the LCD via a framebuffer interface, the Ethernet port, the front-panel interface, and USB ports. Thus far, though, the ability to make use of the device’s integrated FPGA or its capabilities as a functional oscilloscope have not been engineered and implemented – hence the call for assistance.
#mc_embed_signup{background:#fff; clear:left; font:14px Helvetica,Arial,sans-serif; width:100%;}
/* Add your own MailChimp form style overrides in your site stylesheet or in this style block.
We recommend moving this block and the preceding CSS link to the HEAD of your HTML file. */